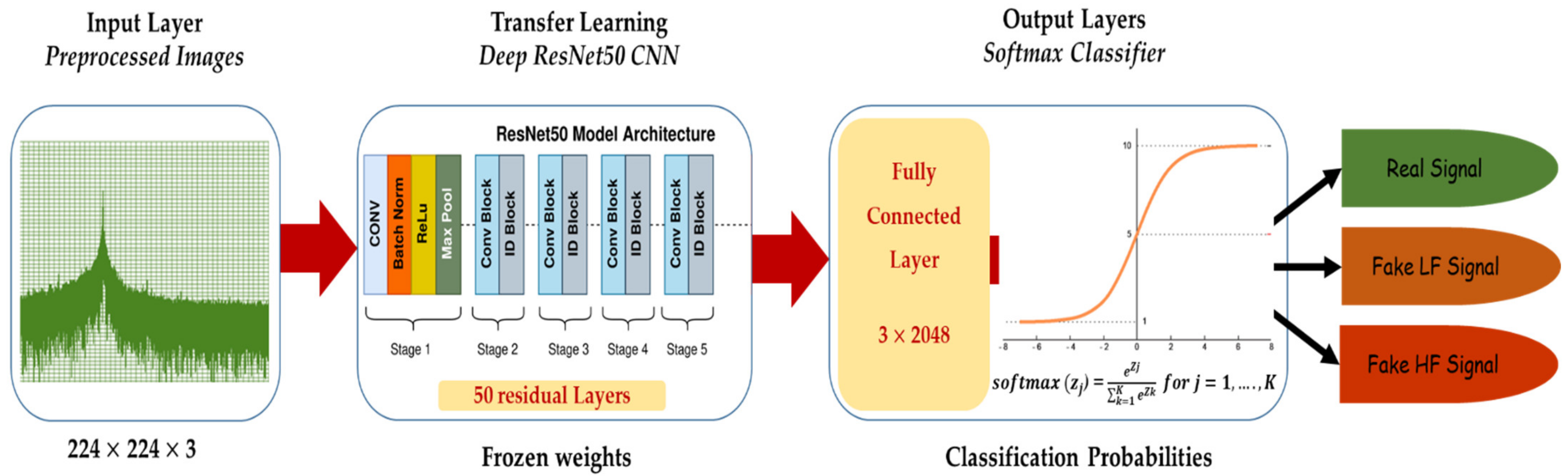
Electronics | Free Full-Text | Detection of Fake Replay Attack Signals on Remote Keyless Controlled Vehicles Using Pre-Trained Deep Neural Network
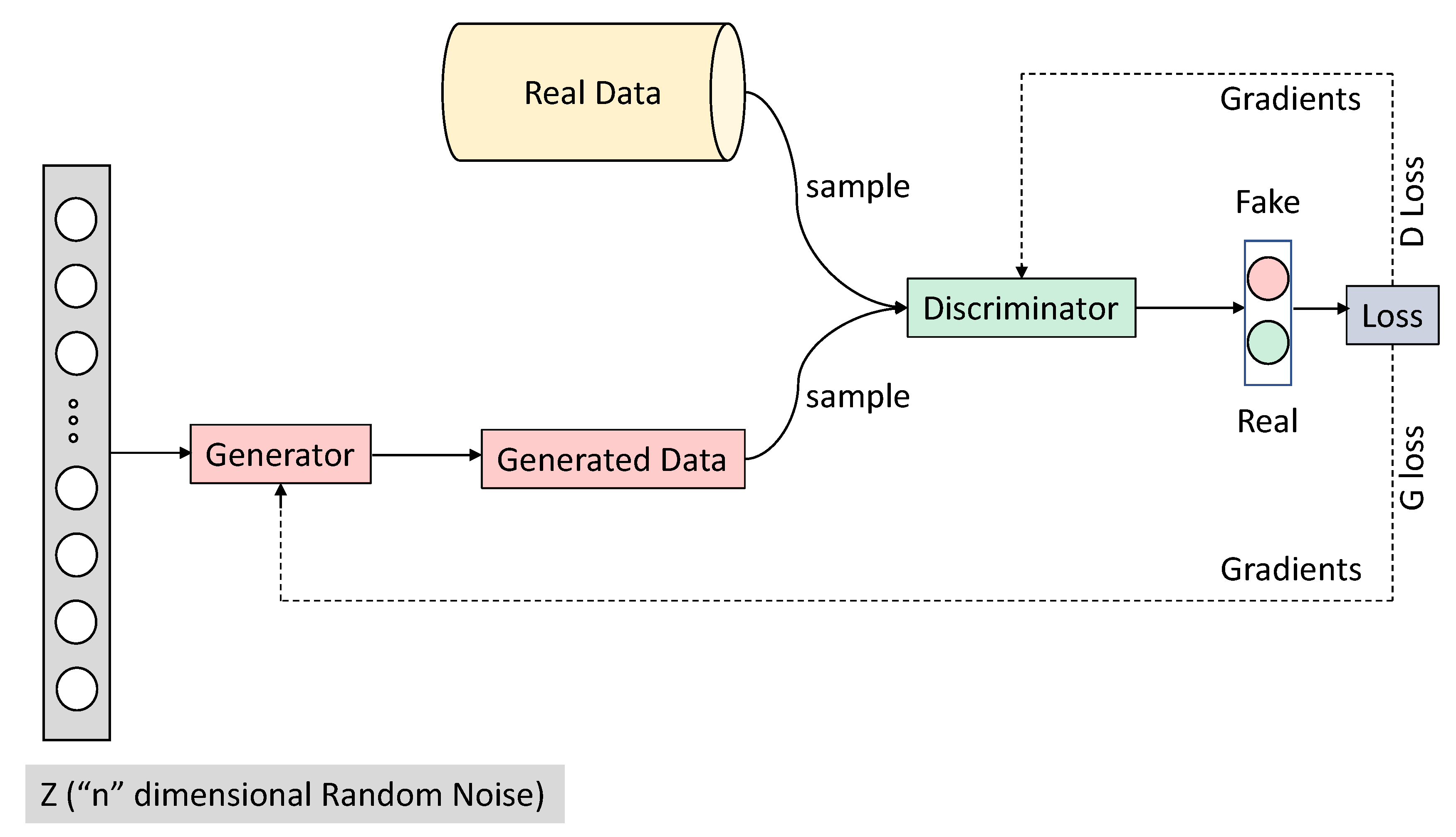
Future Internet | Free Full-Text | Evaluation of Deep Convolutional Generative Adversarial Networks for Data Augmentation of Chest X-ray Images
FactcheckingDay Celebrated by Participants in Internews' Google News Initiative Training - Information Saves Lives | Internews

The CNN architecture of the discriminative network receives the ground... | Download Scientific Diagram
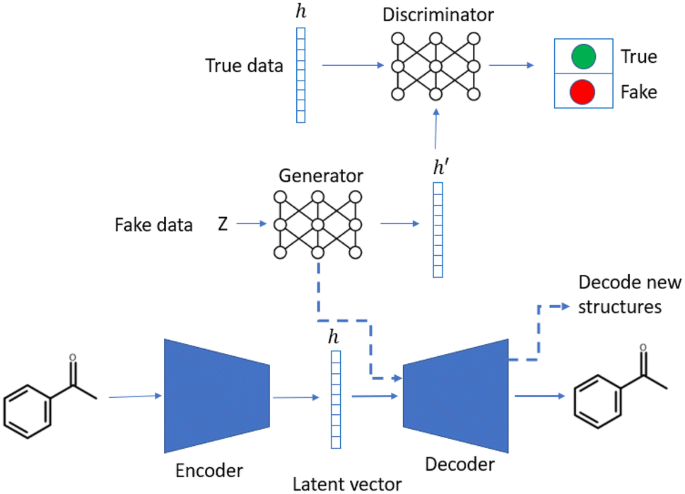
A de novo molecular generation method using latent vector based generative adversarial network | Journal of Cheminformatics | Full Text
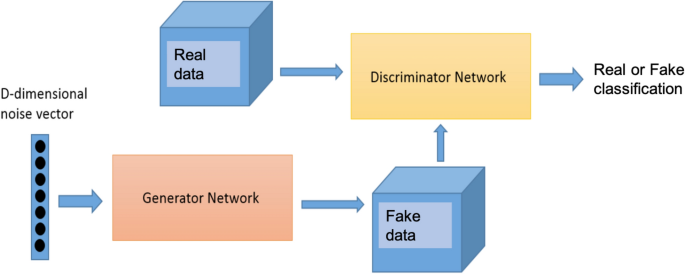
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks | Scientific Reports

Architectural description of the discriminator network used for the... | Download Scientific Diagram


![PDF] Data Augmentation of Room Classifiers using Generative Adversarial Networks | Semantic Scholar PDF] Data Augmentation of Room Classifiers using Generative Adversarial Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f618b37b2b603fd2a4e78efbcb9b30626c564038/3-Figure1-1.png)

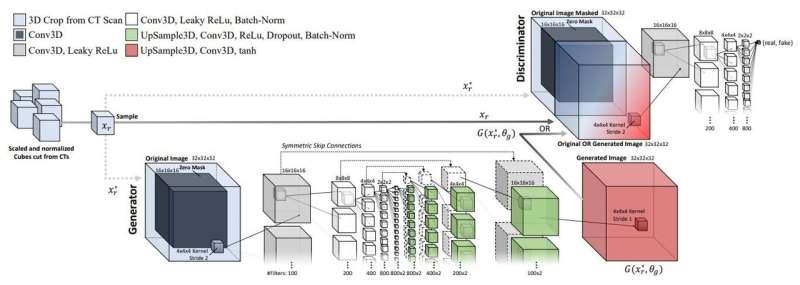


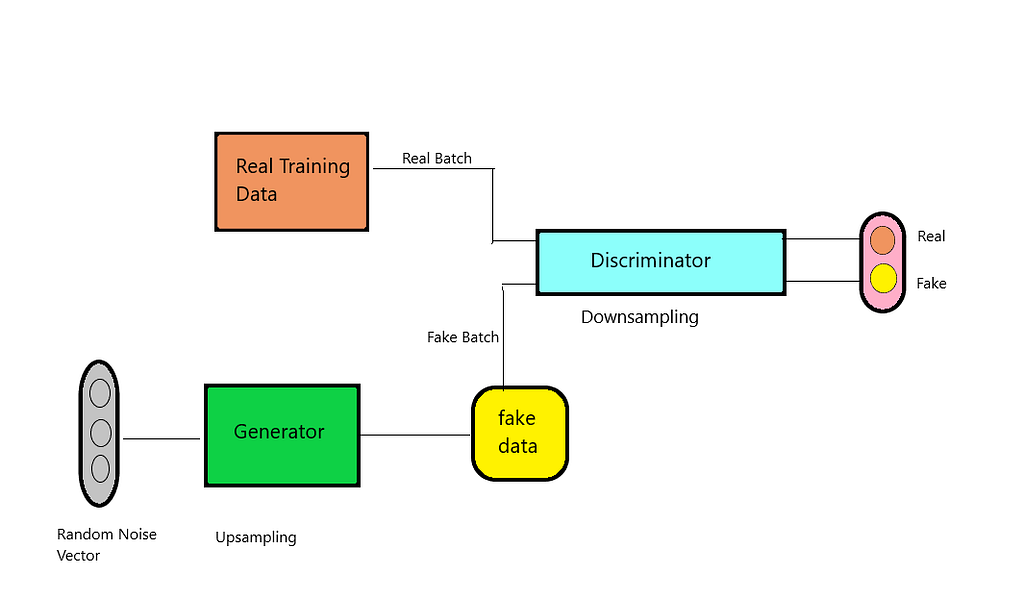




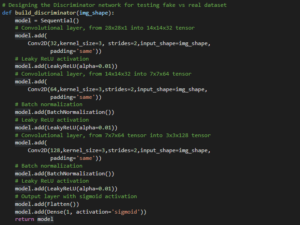

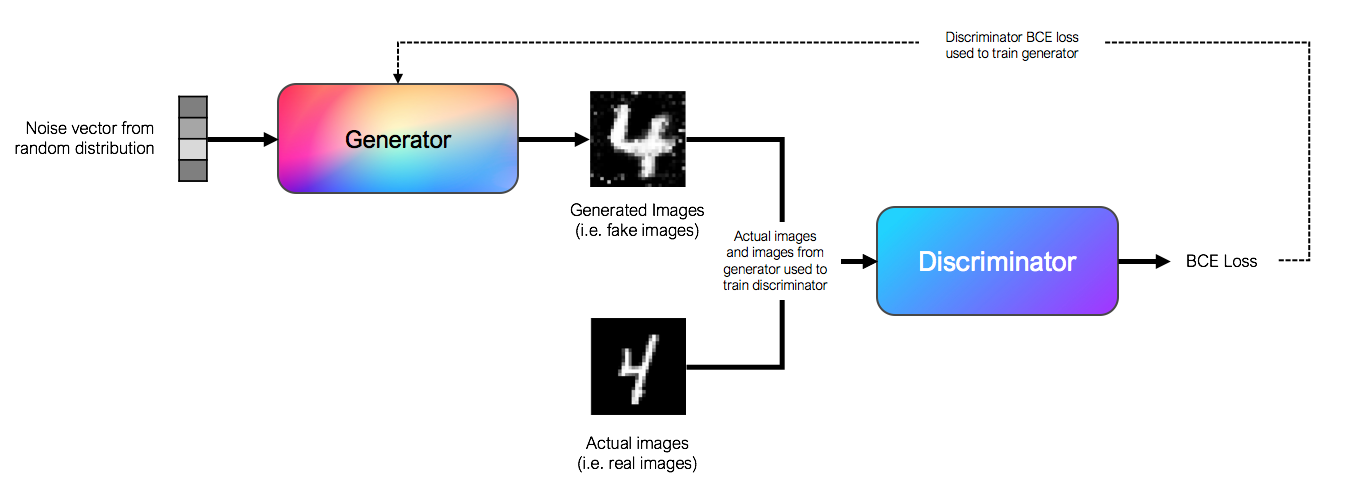
![PDF] Use of a Capsule Network to Detect Fake Images and Videos | Semantic Scholar PDF] Use of a Capsule Network to Detect Fake Images and Videos | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/7a712a43e2f6dcd7692453714eb92e1137d9d06c/5-Figure3-1.png)