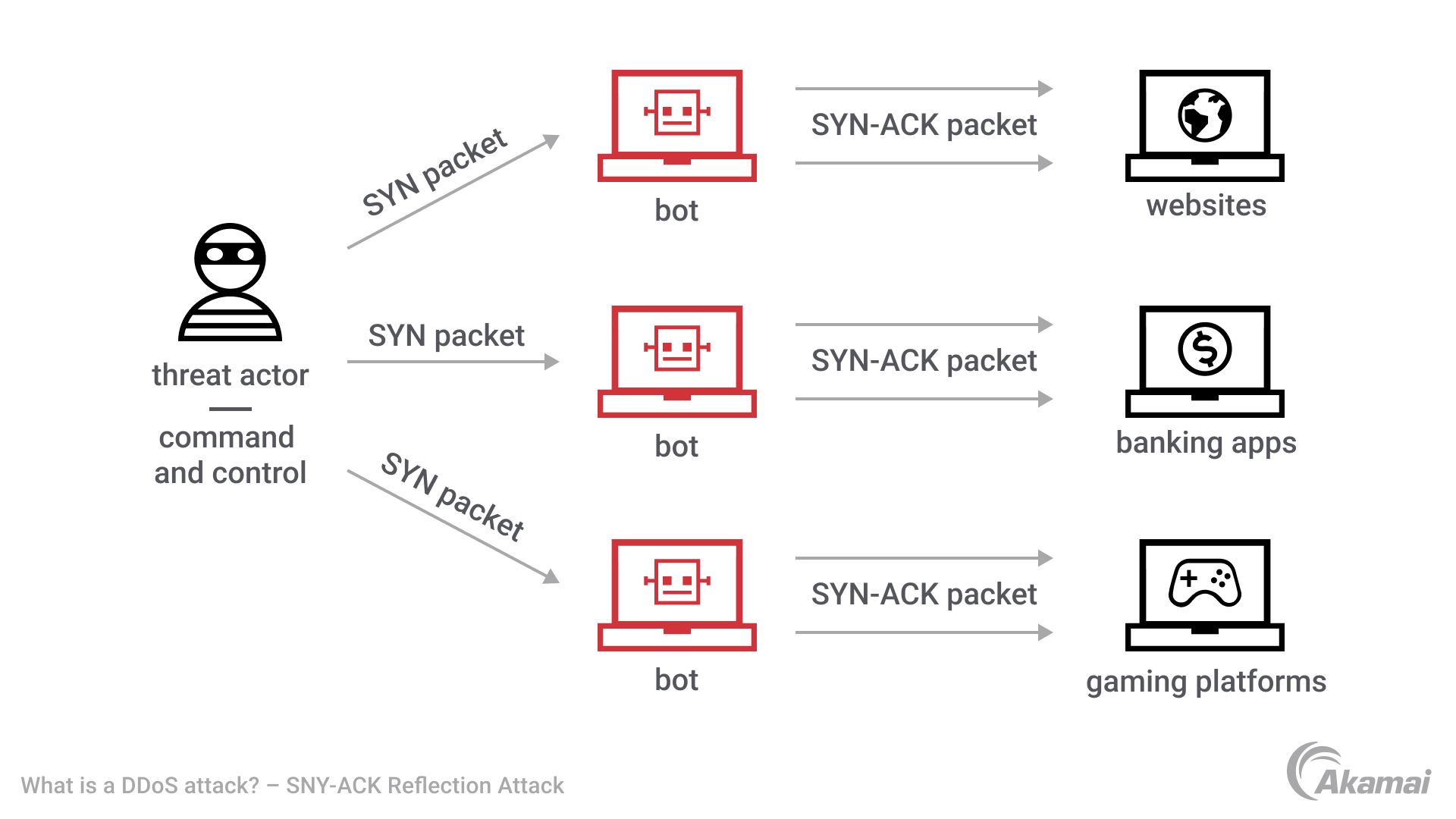
SYN-ACK-ACK proxy flood process. To initiate this attack on Juniper... | Download Scientific Diagram

SYNGuard: Dynamic threshold‐based SYN flood attack detection and mitigation in software‐defined networks - Rahouti - 2021 - IET Networks - Wiley Online Library

Detecting SYN flooding attacks based on traffic prediction - Wang - 2012 - Security and Communication Networks - Wiley Online Library

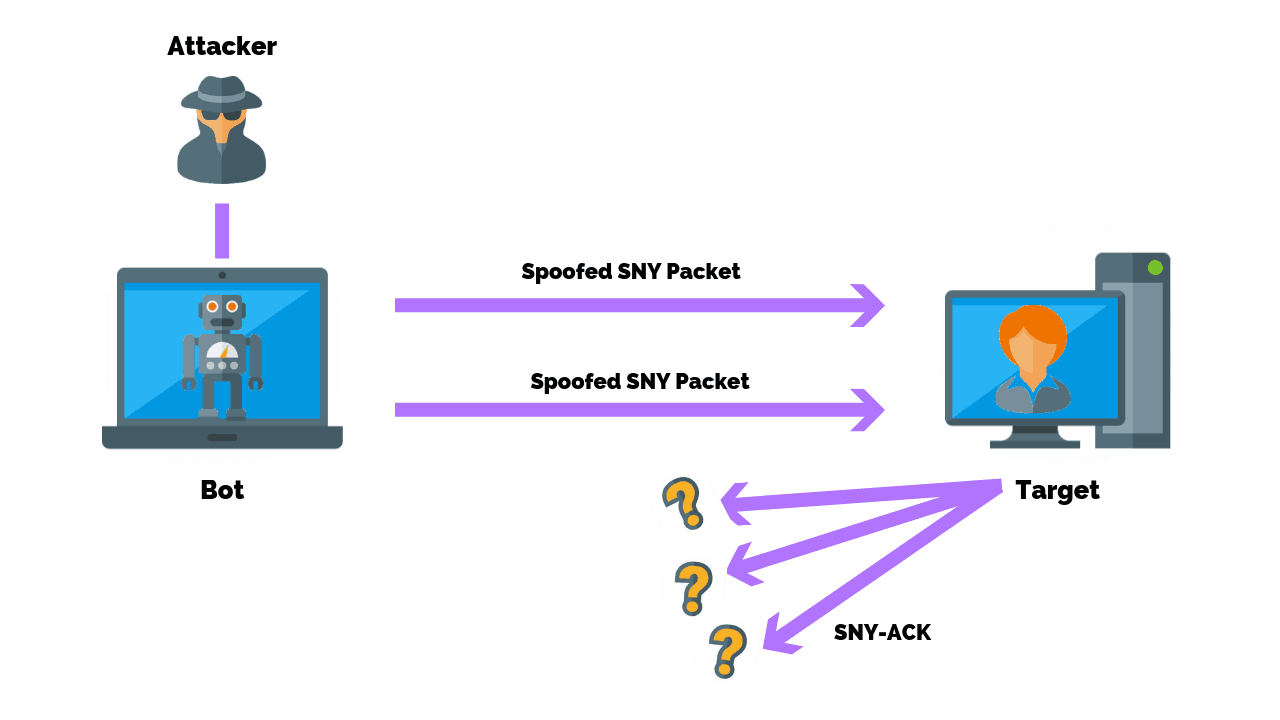


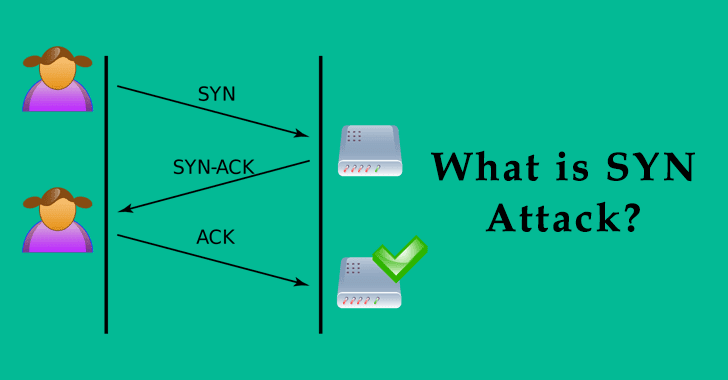




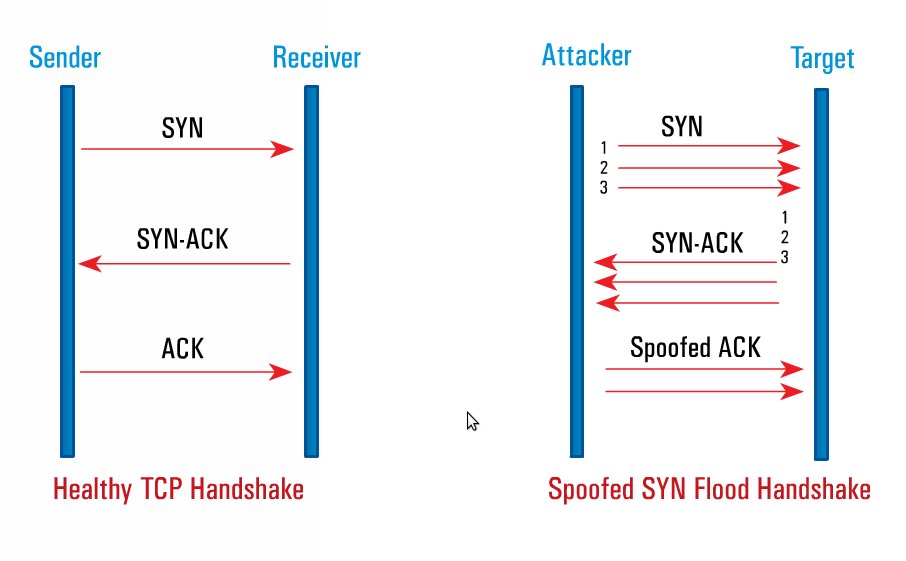
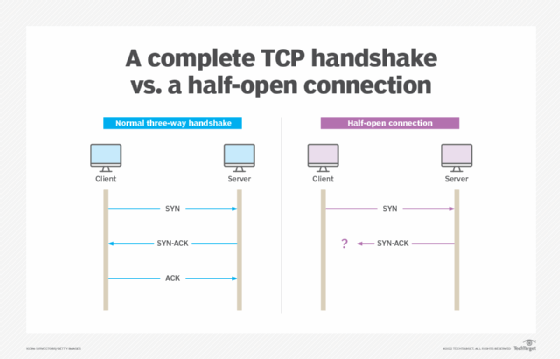


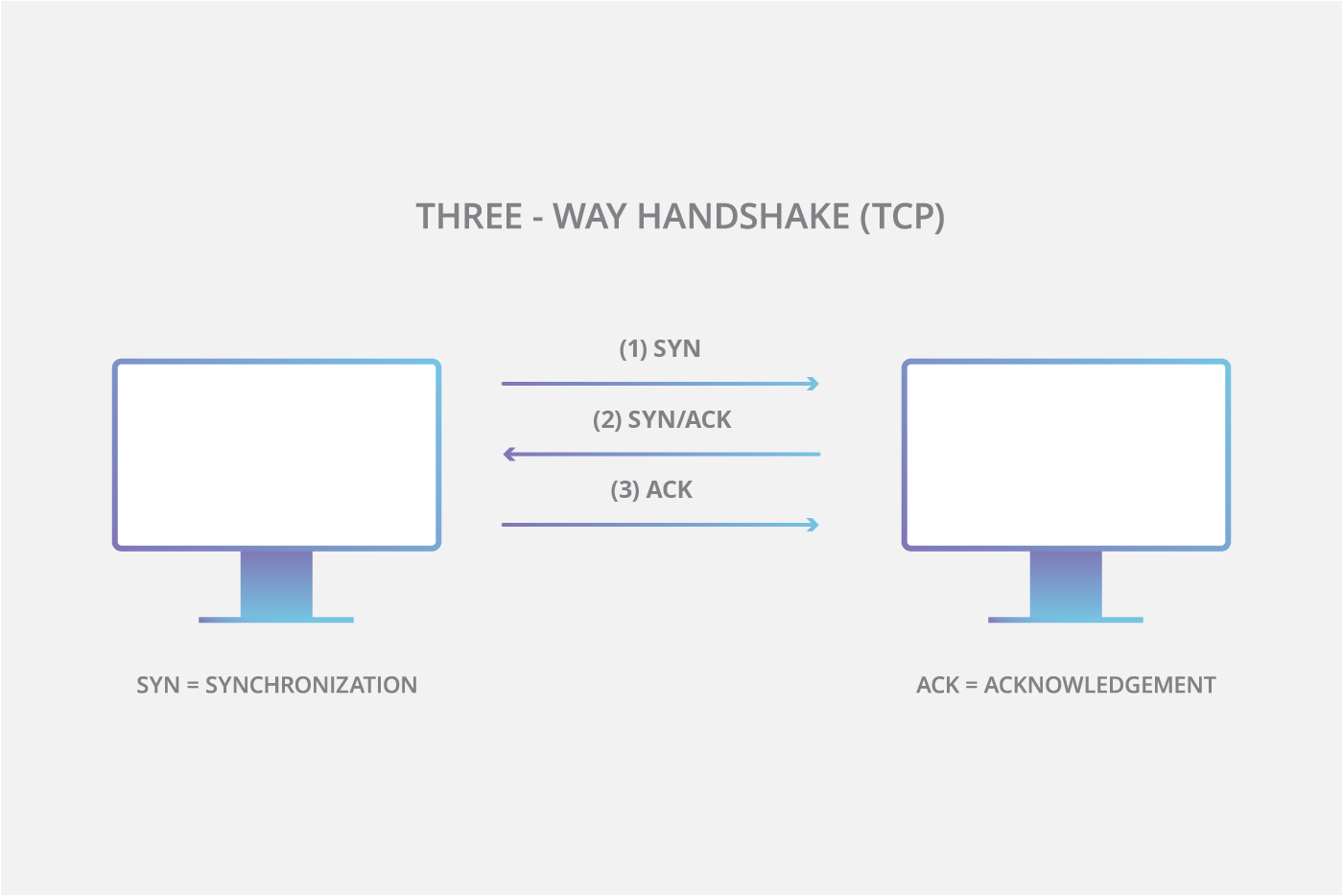
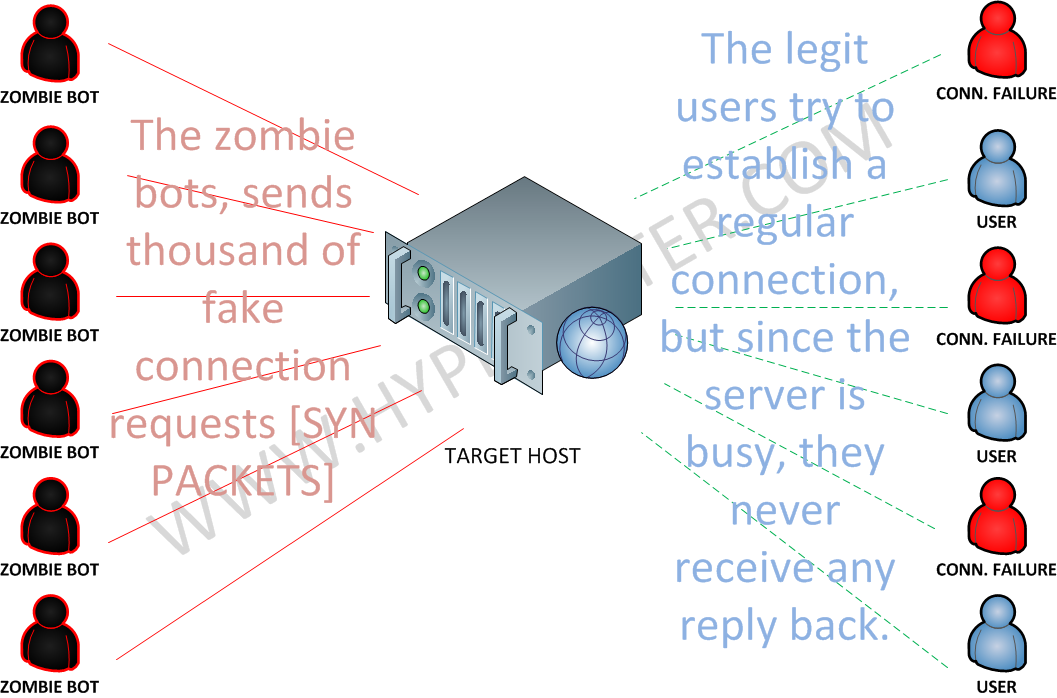
![PDF] TCP-SYN Flooding Attack in Wireless Networks | Semantic Scholar PDF] TCP-SYN Flooding Attack in Wireless Networks | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/82dc0212fc9e66b2430715e6ae4b8210972f8420/2-Figure1-1.png)